
Cyber-criminals have shown once again they’re adept at
exploiting interest in a topical issue, this time it’s the global Coronavirus epidemic
being used to spread malicious activity. Check Point Research has discovered several
spam campaigns relating to the outbreak of the virus and new websites
registered with domain names related to the virus.
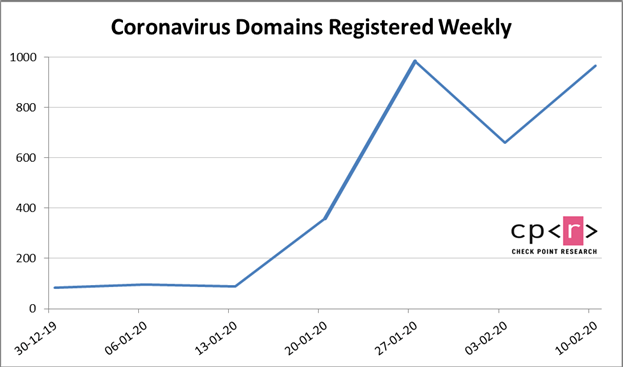
According to their research published in a post on their blog, Check Point found the number of Coronavirus domain names registered weekly peaked at just under 1,000 in the week commencing 27 January with another peak almost as high in the week commencing 10 February. For the period 30 December 2019 to 16 February 2020 there were around 3,200 Coronavirus/COVID-19 related domain names registered.
Many of these domains will probably be used for phishing
attempts note Check Point in their recent blog post. Check Point has seen many
websites known to be related to malicious activities that lure the victims to
their websites with discussions around the virus, as well as from scam websites
that claim to sell face masks, vaccines, and home tests that can detect the
virus.
An example of such a website is vaccinecovid-19.com. It was
first created on 11 February and registered in Russia. The website is insecure
and offers to sell “the best and fastest test for Coronavirus detection at the
fantastic price of 19,000 Russian rubles (about US$300)”.
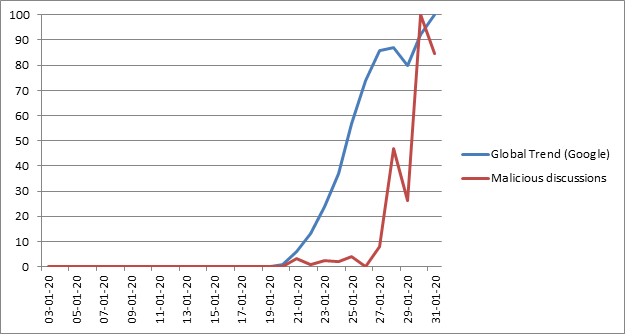
Right after the huge global attention around the
Coronavirus, cyber criminals started using the interest to spread their
malicious activity. Check Point Research’s graph below shows the trend line of
the overall search for Coronavirus by Google Trends, compared to the trends they
observed in social media discussions on cybersecurity and cyber-crime mentioned
in relation to the virus.
In January and February 2020 Check Point also observed the
most prominent Coronavirus-themed campaign targeted Japan, distributing Emotet
in malicious email attachments pretending to be sent by a Japanese disability
welfare service provider. The emails appeared to be reporting where the
infection is spreading in several Japanese cities, encouraging the victim to
open the document for more information. When the document was opened, Emotet
was downloaded onto the victim’s computer.
Emotet is an advanced, self-propagating and modular Trojan.
It was originally a banking Trojan, but recently has been used as a distributor
of other malware or malicious campaigns. It uses multiple methods to maintain
persistence and evasion techniques to avoid detection. It can also spread through
phishing spam emails containing malicious attachments or links.
Check
Point in their blog post have given some recommendations for safe online
behaviour to avoid falling victim to these scam attempts. The recommendations are:
- Ensure you are ordering
goods from an authentic source. One way to do this is NOT to click on
promotional links in emails, and instead Google your desired retailer and
click the link from the Google results page. - Beware of “special” offers.
An 80% discount on a new iPhone or “an exclusive cure for Coronavirus for
$150” is usually not a reliable or trustworthy purchase opportunity. - Beware of lookalike domains,
spelling errors in emails or websites, and unfamiliar email senders. - Protect your organization
with an holistic, end to end cyber architecture, to prevent zero-day attacks
This latest Domain News has been posted from here: Source Link
